|
|
Why are you getting this? You signed up to receive the Tips, asked to stay in touch with Rebecca and/or Privacy & Security Brainiacs (PSB) and allowed receiving the Tips from the reply you received from your accepted link request, or you otherwise asked to receive them. Please read our Privacy Notice & Communication Info at the bottom of this message for more information.
NOTE: A draft version of this month's Tips was mistakenly published to many of our subscribers on August 31. This is the final version. To those of you who received the draft version, and are seeing this online and wondering why is it different from what you received, we apologize for any confusion this caused.
| |
|
Cast Your Vote (but Know the Facts and Watch Your Back!)
If you're in the U.S. you're probably seeing lots of ads containing rhetoric and misinformation about voting fraud. The challenge for all is identifying the facts from the fiction. We've received many questions about this and the related security controls.
The November general election for our local, state and federal political positions is coming up and these claims about voter security and fraud are still pervasive.
While no process or technology, of any kind for any purpose, is 100% secure, the 2020 general elections were determined through audits and assessments by dedicated elections workers, federal and state civil servants, and cybersecurity experts, to have been the most secure in history, from combined results of over a thousand audits and risk assessments.
However, many government leaders, who should be serving as role models, still continue to perpetuate “election fraud” misinformation and falsehoods, which have been debunked many times by the audits, assessments, and verifiable evidence.
I realize this is a contentious topic for many. However, the validity of, and trust in, elections depends upon physical security, technical security, procedural security, auditability, and verifiable data created to reflect the activities that have truly occurred. Because of this, I believe elections security is an important topic to tackle, and to provide the verifiable facts for our readers' consideration.
Here are some facts important to know up front: Voting machine equipment, standards and procedures vary greatly from state to state, and even county to county. Regarding standards, some states adopt federal standards, some develop their own standards and others use a hybrid of both approaches.
In light of the diversity of the over one hundred thousand voting machines used throughout the U.S., none of which are connected to the internet and rarely to each other, and considering the different voting procedures throughout the states and territories, committing widespread fraud would be virtually impossible.
I discussed some of the most widely claimed voting fraud falsehoods in my September episode (first airing on September 3) of the Data Security & Privacy with the Privacy Professor show. This is the most recent of our numerous episodes we've done on elections security.
In this issue, we include some of the many questions we've received about election security, along with other timely questions and topics.
Do you have stories, examples, or concerns about the topics covered in this issue that you would like for us to provide feedback on? Send them over! We may discuss it in an upcoming Tips.
| | |
|
Rebecca
We would love to hear from you!
Did you find the tips we provided useful? Did you like this issue? Do you have questions for us to answer? Please let us know at [email protected].
| |
Here are more memorable moments from my travel to national parks with my son. | |
My son takes in amazing Goosenecks State Park, Utah | |
This highway and monuments were in an iconic scene of "Forrest Gump" | |  |
My son and I at Canyonlands National Park in Utah | | |
|
September Tips of the Month
- Monthly Awareness Activity
- Privacy & Security Questions and Tips
- Data Security & Privacy Beacons*
- Privacy and Security News
- Where to Find the Privacy Professor
| |
Monthly Awareness Activity | |
|
The third Thursday in September each year is the International Day of Listening. What a perfect day to inject some security and privacy awareness into communications with your friends, family, customers, co-workers, and patients!
Here are a few activities to consider.
Listen for the clues of scammers and social engineering (often called phishing), in unsolicited calls, especially those that ask for personal information. Beware of:
- Unsolicited calls offering too-good-to-be-true deals, such as free products and/or vacations, cash prizes, medical devices, preapproved loans, etc.
- Unsolicited calls claiming to be from the government, city utility, or a tech giant. These types of organizations rarely call unless they’ve communicated with you in other ways first.
- Unsolicited calls claiming to be from charity fundraisers, most commonly after disasters, or during holidays.
- Recorded calls claiming you owe money, or that you’ve won something. These are likely robocalls, and if you’ve not agreed to receive such calls, they are usually illegal and scams (unless they are from a non-profit or political campaign).
- If you work in customer service, a call center, or a similar type of organization, listen carefully and document callers who tell you that they are concerned that others are getting into their account, especially for IoT products such as smart cars, etc. Take appropriate actions, such as reporting to your manager.
A Real-Life Example of an IoT Phishing Scam
I was an expert witness for a case where the owner of a smart car called the call center multiple times, first expressing concern that her ex-partner was accessing her account to track her. Then, she asked again multiple times, to completely disable the location tracking capabilities. However, her ex-partner then called in and successfully asked for access. He tracked his ex down, assaulted her, and almost killed her. If customer service had listened, documented the requests and concerns, and taken the right action, the crime could have been avoided. Scary, but true!
|  | |
|
Privacy & Security Questions and Tips
Rebecca answers hot-topic questions from Tips readers
September 2022
| |
With general elections quickly approaching in the U.S., we thought now would be a perfect time to answer a few of the many voting and elections security questions we’ve been getting. We also received many questions from readers about topics we covered in the August edition of the Tips, so we are including a couple of those as well. Please keep your questions coming! | |
|
Q: I just received two postcards with voter registration information from a major political party, reminding me to vote and confirming registration data. One of the cards was addressed to my late wife. Is she still considered a registered voter?
A: My condolences for your loss.Thanks for asking such a great question. All political parties obtain voter registration records from each state's Secretary of State (SoS) office. This is a legal and widespread practice by all political parties and candidates. They've honed their messaging so they are speaking truthfully, but providing you with information that is taken out of context and often very misleading.
Because a political party mailed the postcards to your house, I anticipate they are promoting their candidates, and want you to sign-up to vote, and/or engage in some other activity. This is expected. U.S. laws generally allow for political parties to directly contact people without first getting express permission.
However, based on what you described, and what I've seen throughout the years as common (and basically de facto) practices within each of the political parties, they are likely adding newly-collected voter registration data from the SoS and simply adding it to their long-established voter registration database. I've never found over the years any political party that actually removes data from their registration lists. The voting experts I contacted also corroborate this practice by many-to-most-to-all of the political parties.
I know from a long-time acquaintance here in Des Moines, IA, who goes around urging people to vote on behalf of her political party, that she believes she is using old registration data for her door-to-door campaigning. "The more people we speak with, the merrier!" she says.
Did it come from the government; from their "public records"? Yes. But when? 5 years ago? 10 years ago? After getting your message, I asked my acquaintance about this, and she said she wasn’t sure, but from what she knows she thinks they are just adding the new data they get to the existing data they’ve got because “the lists get longer every year.”
So, while political parties DO collect publicly available voter registration records from the SoS, they reportedly rarely, if ever, remove any of those records from what they've amassed over the decades. Any political party can spin the use of such old data to their advantage when it comes to trying to get the public to believe a conspiracy theory or promote some other agenda.
To be fair, most of those going door-to-door are volunteers who were simply given a list of people to contact and told they were the "official voter records," so I doubt if most of them realize that they have old, outdated, and no longer valid voter registration data that is mixed in with current data.
Iowa has some specific procedures for regularly updating its voter registration databases that *ARE* used for actual voting purposes. They include removing a voter from the official registration list if the voter:
- Dies. This is confirmed regularly by running the official voter registration database against Iowa death records
- Confirms in writing a change of address outside the county
- Requests removal in writing
- Doesn't vote in two general elections and becomes inactive
- Is convicted of a felony and hasn't had their voting rights restored
- Is judged to be incompetent by a legal entity
- Submitted a jury disqualification form to an Iowa court because they aren't a citizen
So, even if a political party campaign volunteer or employee indicates they got the data from the "public records," what they are NOT telling you (knowingly or unknowingly) is that the OFFICIAL voter registration lists are updated by the SoS regularly, to help ensure no one who has moved, died, etc. will be allowed to vote by mail, or by in-person balloting. The SoS has oversight of ALL voting activities, applying the same rigor to mail-in voting as for in-person voting.
See all the procedures for all the states here.
Bottom line: Those volunteers for political parties are NOT necessarily, or even likely to be, using the same up-to-date registration files as the SoS uses for official voting, even if the data originally came from the SoS at some point in time. In fact, based on my findings, and the research from full-time voting experts, political parties rarely follow consistent, or any, procedures to remove people from their voter registration records. As my long-time acquaintance told me, “Hey, the more people we can speak with the merrier!”
| |
|
Q: How secure is absentee and mail-in voting?
A: Absentee and mail-in ballots are paper ballots that are completed by the voter. At least 44 states require signature verification. Nine states and the District of Columbia automatically send these ballots to registered voters. None are sent to non-registered people, including the deceased, pets, and fictional characters.
If someone mailed in their ballot early and then died before Election Day, their vote might be counted.
Mistakes can be made by non-profits and political party groups that use outdated databases (see above) to mail ballot applications. These applications are NOT ballots, however.
Since 1991, only 11 cases have been reported in which someone filled out an absentee ballot on behalf of someone who died.
Most states have established procedures that enable voters to track when their ballots were mailed from the election office, when they were delivered, and when the election office receives completed ballots.
On rare occasions, ballots needed to be recalled. In 2020, Michigan sent 400 absentee ballots on which an incorrect candidate name appeared. It was quickly caught and corrected.
In short, voting by mail is one of the most secure ways to vote.
| | |
Q: Can voters make copies of their mail-in or absentee ballots and submit multiple votes?
A: They can try, but voting security procedures and technology will identify such attempts. For example, ballot scanners use specific paper types, which are not available to the general public.
Genya Coulter is an election professional, election security expert, and one of the Top 25 Women in Election Security and Tech. She has been a guest on my show multiple times. Hear some of her insights, including information about attempted voting more than once, in the April 2021 Episode of my Show.
| |
Q: I use the MetaMask Wallet for cryptocurrency transactions. But I recently got this e-mail? Will I lose all my money? | 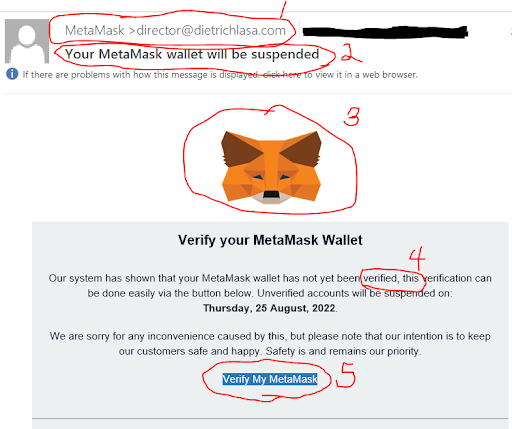 | |
A: The above is actually a phishing message that has been circulating since early 2022 and is well-constructed to trick recipients! If you were to click on it, your information would be stolen, along with the crypto in your account. Recipients who clicked also were the victims of unauthorized purchases, changed passwords, identity fraud and theft, unauthorized or illegal access to computers, and malware.
Here are the red flags:
- The e-mail doesn't come from MetaMask.com. It's from dietrichlasa.com.
- When unsolicited messages say an account will be suspended, people tend to panic and react. This is a common phishing tactic.
- The logo is squashed and unprofessional.
- Writing errors or incorrect grammar (which, in this case, is a misplaced comma).
- When the recipient hovers over the blue bar, the link goes to secunderabadclub dot org, which is flagged as "risky" by our anti-virus software.
| |
|
Q: Following up on last month's Tips...what health monitoring apps are the worst for women's health privacy?
A : That's a very timely question with an eye-opening answer. Gizmodo just reported their research, including which data brokers sell health data. A whopping 32 brokers sell access to mobile IDs of 2.9 billion women's health profiles, representing 3.4 billion people in total. Read the report here. The data is collected through apps, digital coupons, website logs, social media sites, and other online locations. See the list of brokers below.
| |
|
You can find the names of the apps and organizations from where these 32 data brokers collect data by reviewing the data brokers' sites.
For example, the image below is a screenshot from the Dstillery site. You can see how their information is collected. Like most data brokers, they use AI to pull out health insights, even if the apps they are using as sources were not created specifically for health tracking services.
This common practice in data farming is currently not regulated in the U.S.
| |
|
Data Security & Privacy Beacons*
People and places making a difference
| |
-
FedEx for their Updated Privacy Notice for FedEx Delivery Manager and clearly communicating the update to their customers.
-
Self Magazine’s article by Maggie O’Neill describing, at a high level, “Here’s How to Track Down Your Childhood Vaccine Records." Try these tips if your mom has no idea.” After you get your records, make a copy and put it in a secure place, such as in your bank deposit box. Then ask the sources that provided them to you to delete/destroy them, and to provide a certificate of destruction, or attestation from the healthcare provider's, agency's, etc., highest management that your records were indeed irreversibly destroyed.
-
The Department of Justice (DoJ) for their work in successfully putting into prison for 46 months, Jack Owuor, 25, of Paramount, California, and Timothy Ingram, aka Bleezy, 29, of North Hollywood, California, both members of a network of criminals who, through extortion and fraud, induced elderly Americans across the United States to pay up to tens of thousands of dollars each to help their purported grandchild or other loved one through their “Grandparent Scam.” Owuor and Ingram pleaded guilty to conspiracy under the Racketeer Influenced and Corrupt Organizations (RICO) Act. The DoJ also provides help through their National Elder Fraud Hotline: 1-833-FRAUD-11 (1-833-372-8311), which is staffed by experienced professionals who provide personalized support to callers by assessing the needs of the victim and identifying relevant next steps.
-
Nic Fab for publishing his detailed research about 10 different privacy search engines and their associated privacy-protecting capabilities.
-
Downdector for providing information about sites and services that are down or having problems.
-
CyberSecurityDegrees for providing a listing of Information Security Degree Programs.
-
WSJ Nicole Nguyen for her article, "Spam Texts Are Surging. Here’s How to Avoid Being Swindled." Scam robotext messages have exploded, but you can protect yourself by not clicking links, never texting back, and turning on your phone’s unknown-message filter.
-
The Federal Trade Commission for their Mobile Health Apps Interactive Tool providing direction to app developers about the federal laws they need to make sure their apps comply with.
-
Citi for sending alerts to their customers about current scams to be aware of, such as this current Zelle scam (below).
| |
*Privacy Beacons do not necessarily indicate an organization or person is addressing every privacy protection perfectly. It simply highlights a noteworthy example of privacy-aware practices. | |
|
Privacy & Security News
Visit the PSB News Page often!
| |
|
Since our last Tips alert, we've added a wide range of useful information to our Privacy & Security Brainiacs (PSB) News Page. It's organized by topic, so you can find what's most relevant or interesting to you. You'll also find this separate page for IoT security and privacy news. Other timely topics include Log4j security and privacy vulnerability, patches, and exploits.
Please follow the PSB page on LinkedIn, and don't hesitate to message us with your questions and concerns.
You can also check out our website, where we post 3-4 times a week.
| |
|
HIPAA Basics for Business Associates is getting great reviews!
Feedback on our new online class has been stellar, with "students" telling us that the real-world examples have helped them beef up their own practices and protect their family and friends.
| |
|
Master Expert Program
Amp-up your knowledge to ensure safety and build your care with the brilliant Dr. Mich Kabay, our first Master Expert leader and instructor. Former director of the NSA-accredited Norwich University Master of Information Security and Assurance Program, he will teach Secure Coding and Software Quality Assurance.
Open to all levels, the program will give you 2 continuing education credits (CPEs) and a Professional Certificate. Ask about our beta discount!
| |
Where to Find the Privacy Professor | |
|
|
|
If you haven't checked out Rebecca's radio show, Data Security & Privacy with the Privacy Professor, please do. Guests discuss a wide range of
real-world topics within the data security and privacy realm.
Latest Episode
First aired on Saturday, August 6, 2022
Dr. Micah Kabay
Privacy Breaches Can Be Prevented with Secure Coding
Dr. Mich Kabay describes how some of the largest privacy breaches in history resulted from not using secure coding concepts. From women’s lingerie to allowing health data to be stolen, and more, Dr. Kabay will not only describe the real-life vulnerabilities, but also how each could have been prevented, including for CISA’s Top 25 Most Dangerous software weaknesses.
Next Episode
First airing on Monday, September 3, 2022
Marci Andino
Free Election Security Help for All U.S. States and Territories
Dr. Marci Andino talks about how our country is securing elections processes and voting machines. She debunks some of the common voting fraud lies, using facts and trends.
| | | |
I'm leading this esteemed FutureCon panel discussion, providing the latest insights on cybersecurity. | |
|
Don't miss this timely webinar on women's health privacy and you can collect CPE credit.
The controversial Dobbs decision, overturning Roe v Wade, is the topic for this provocative online session, covering implications for HIPAA compliance, employee security and benefits, and privacy of women's health data.
| |
|
Permission to Share
If you would like to share, please forward the Tips message in its entirety. You can share excerpts, as well, with the following attribution:
Source: Rebecca Herold. September 2022 Privacy Professor Tips. www.privacysecuritybrainiacs.com
NOTE: Permission for excerpts does not extend to images.
Privacy Notice & Communication Info
You are receiving this Privacy Professor Tips message as a result of:
1) subscribing through PrivacyGuidance.com or PrivacySecurityBrainiacs.com;
2) making a request directly to Rebecca Herold; or
3) connecting with Rebecca Herold on LinkedIn.
When LinkedIn users initiate a connection with Rebecca Herold, she sends a direct message to each of them when accepting their invitations. That message states that each month, to support the LinkedIn networking purpose and goals, and to stay in touch with her links, she sends her LinkedIn connections one security and privacy tips message via email each month. If they do not want to stay in touch with her in this way, LinkedIn connections are invited to let Rebecca know they do not want to get email messages from her by responding to that LinkedIn message or contacting her at [email protected].
If you wish to unsubscribe, just click the Safe Unsubscribe link below.
| | | | | |